- For Business ›
- Blog
The Sensible Weather Blog

Sensible One of Fast Company's Most Innovative Companies
Sensible Weather named one of FastCompany's Most Innovative Companies in the world for 2025.

Sensible Announces Partnership with Sabre Hospitality
Sensible Announces Partnership with Sabre Hospitality

Sensible Partners with Inntopia to Offer Weather Guarantees for Skiers
Sensible Weather Partners with Inntopia to Offer Weather Guarantees for Skiers
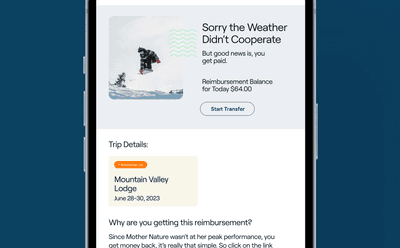
What is a Weather Guarantee?
Weather conditions can have a significant impact on the guest experience, especially for outdoor activities. The Weather Guarantee from Sensible Weather is a…

How Weather Guarantees maximize revenue for theme parks and attractions
How Weather Guarantees maximize revenue for theme parks and attractions

Sensible One of Fast Company's Most Innovative Companies
Sensible Weather named one of FastCompany's Most Innovative Companies in the world for 2025.

What is 1.5mm of Precipitation Per Hour?
1.5mm per hour of rain, what does 1.5mm of rain look like.

Sensible Partners with Inntopia to Offer Weather Guarantees for Skiers
Sensible Weather Partners with Inntopia to Offer Weather Guarantees for Skiers

Sensible Weather Partners with Leap Event Technology
New Partnership Brings Peace of Mind to Event-Goers, Offering Automatic Weather Guarantees for Outdoor Events
Loading...
Stay in the know
Subscribe to our newsletter to receive the latest updates from Sensible Weather, right in your inbox.
